29.06.2021
Fraunhofer researchers hack Bluetooth locks from Tapplock
Fraunhofer SIT researchers find two serious security vulnerabilities
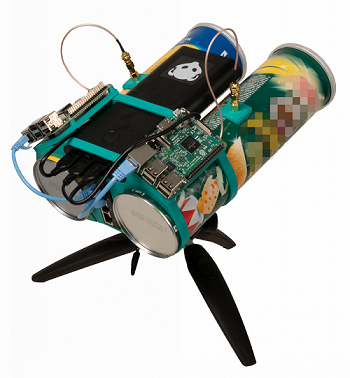
A homemade directional antenna made of potato chip cans and two commercially available mini-computers are enough to hack Bluetooth locks made by the US manufacturer Tapplock in seconds, as proven by researchers at the Fraunhofer Institute for Secure Information Technology SIT in Darmstadt. The manufacturer was informed about the vulnerabilities and has since fixed them in one of its models.
Cumbersome rummaging around for the bike lock or locker key is no longer necessary with a modern Bluetooth lock: You simply close the lock using your fingerprint or via an app on your smartphone, which is connected to the lock via Bluetooth Low Energy (BLE). But even these locks can be picked, as a group of scientists from Fraunhofer SIT has now discovered. They examined two Bluetooth locks from the manufacturer Tapplock, namely Tapplock ONE and Tapplock ONE+, and found two serious security vulnerabilities in both models. These objects allow attacks that can completely undermine the security mechanisms of the locks without leaving any traces of intrusion. Both attacks can be carried out with minimal technical and financial resources. An attack tool was used for this purpose, which the scientists had built from potato chip cans and commercially available mini-computers (Raspberry Pi), among other things.
Attack with directional radio antenna from chip cans
The first attack scenario uses a man-in-the-middle attack: Here, the attacker switches into the Bluetooth connection established between the lock and the attack victim's smartphone while locking his lock. Thus, the data that is normally exchanged directly between the lock and the smartphone also passes through the attacker. Once the owner has left, the attacker maintains the connection to the lock and simply resends the communication data that had been just sent to the lock, which is necessary to open and close the lock. The lock opens and the attacker has achieved his goal.
Replay attack picks the lock in under a minute
The second vulnerability found can be exploited via a so-called replay attack. To do this, it is necessary to record the locking process once, using a challenge-response method, for example, with the self-made attack tool. This time, the attacker no longer needs a constant connection to the lock, but simply waits until he has free access to the lock and launches any number of queries to the lock. This is possible because the lock did not have any blocking or delay built in even with many queries. It takes about 30 to 60 seconds for the previously recorded challenge to repeat. With the recorded response, it is now possible to open the lock any number of times without the rightful owner noticing.
The Fraunhofer SIT researchers reported these vulnerabilites to the manufacturer Tapplock as part of the responsible disclosure process. The manufacturer has closed the vulnerabilities in the Tapplock One+ model, but the Tapplock One model did not receive an update.